Hackers don’t need you to click anything to steal your data anymore. They’ve developed advanced tricks that exploit software flaws, unsecured networks, and even everyday habits. Here’s how these silent attacks work—and what you can do to stay safe.
Zero-Click Exploits

Credit: pexels
Some hackers don’t even need you to click a bad link to break into your device. They take advantage of hidden software flaws in apps, emails, or even system updates to install malware or spy on you remotely. To stay safe, always keep your devices updated, turn off auto-preview for messages, and use security tools that detect suspicious activity.
Man-in-the-Middle Attacks

Credit: Getty Images
You think you’re securely logging into your bank, but a hacker is secretly reading everything you type. That’s what happens when cybercriminals intercept your data by setting up fake networks or taking advantage of weak encryption. The best defense is to use a VPN, avoid public Wi-Fi, and always enable multi-factor authentication for extra security.
Session Hijacking

Credit: DragonImages
Hackers don’t always need your password to break into your accounts. They can steal authentication tokens from unsecured websites or public networks, which allows them to log in as if they were you. To prevent this, always log out of sensitive accounts when you're done, stick to secure websites with HTTPS, and regularly clear your cookies.
Drive-By Downloads

Credit: Getty Images
Just visiting the wrong website can be enough to infect your device with malware—no clicks or downloads required. Hackers exploit outdated browsers, plugins, or hidden software weaknesses to sneak harmful code onto your system. Protect yourself by keeping your browser updated, using an ad-blocker, and disabling unnecessary plugins.
Evil Twin Wi-Fi Networks

Credit: kittichai boonpong's Images
Hackers can set up fake Wi-Fi networks with names that look just like trusted hotspots, thus tricking your device into connecting automatically. Once you’re on their network, they can steal your login details or install malware. Always verify network names before connecting, disable automatic Wi-Fi connections, and use a VPN.
Keystroke Eavesdropping

Credit: Canva
Some malware can secretly record everything you type, including your passwords and private messages. These attacks often happen when you download infected software or plug in a compromised USB device. To protect yourself, install trusted security software, use two-factor authentication, and check for unknown programs running on your system.
Browser Fingerprinting Spoofing

Credit: Getty Images
Websites and hackers alike can track you by analyzing your browser’s unique settings, extensions, and even your device’s configuration. Cybercriminals use this fingerprint to bypass security checks and launch targeted attacks. Reduce your exposure by switching to privacy-focused browsers, using extensions that randomize your fingerprint, and turning off settings that reveal too much about your device.
Malicious QR Codes

Credit: DragonImages
Not all QR codes are safe. Hackers can create fake ones that redirect you to scam websites or trigger hidden malware downloads the moment you scan them. Before scanning, make sure the source is trustworthy, use a QR scanner that previews links before opening them, and avoid scanning codes from random posters or emails.
Web Skimming

Credit: Getty Images
Even legitimate-looking online stores can be compromised by hackers who insert sneaky code into payment forms, stealing your credit card details in real time. Since everything appears normal, you won’t know your info has been stolen until it’s too late. Stay protected by using virtual credit cards, monitor your bank statements for suspicious charges, and opt for secure payment methods like PayPal whenever possible.
Default Password Exploitation

Credit: Getty Images
Many routers, security cameras, and smart devices still use factory-set passwords that hackers can easily find online. They scan for these unsecured devices and take control without breaking a sweat. Always change default passwords when setting up a new device, use strong and unique passwords, and enable two-factor authentication when possible.
Unsecured Bluetooth Connections

Credit: pexels
Leaving Bluetooth on when you don’t need it is like leaving your front door unlocked—hackers can use it to steal data, track your location, or even install malware. It’s highly recommended to turn off Bluetooth when you’re not using it, set your device to non-discoverable mode, and remove old or unknown paired connections.
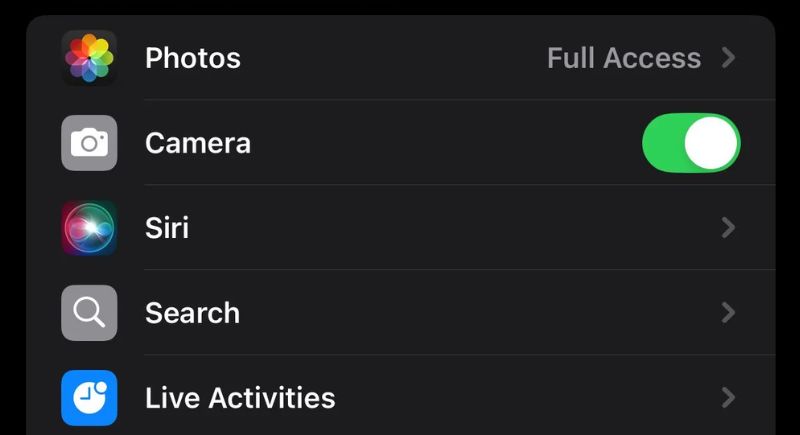
Unauthorized App Permissions
Credit: Reddit
Some apps ask for way more access than they actually need—tracking your location, reading messages, or even using your camera without you realizing it. Check app permissions before installing anything, deny unnecessary access, and only download apps from trusted sources like official app stores.
Public Charging Station Attacks ("Juice Jacking")

Credit: Wikimedia Commons
Using a free charging station at the airport or a coffee shop might seem harmless, but some hackers modify USB ports to steal your data or install malware on your device. To avoid this, bring your own charger, use power-only USB cables, or rely on a portable battery pack instead.
Compromised Supply Chains

Credit: Getty Images
Hackers don’t just attack individuals—they also infiltrate software updates, hardware components, or third-party services to spread malware before a product even reaches consumers. Even trusted companies have been victims of these attacks. Only update software from official sources, verify new devices before installation, and monitor for unusual activity after applying updates.
Social Engineering Tactics

Credit: Getty Images
Sometimes, hackers don’t need fancy tech—they just trick people into handing over personal information. Fake customer service calls, urgent scam emails, and impersonation schemes are all designed to get you to reveal passwords or security codes. The best defense is so stay skeptical. Verify requests through official channels and avoid sharing sensitive information with anyone who contacts you unexpectedly.